Command Line One Time Passwords for Microsoft Multi-Factor Authentication
Posted on March 28, 2025This post explains how to generate verification codes via the command line in Linux and MacOS to log into websites that use Microsoft mutli-factor authentication (MFA).
It avoids the need to use a MFA smartphone apps like Microsoft Authenticator, bypassing 2FA fatigue. Our phones are not always nearby or may not have an internet connection.
Steps
First, you need to install the OATH toolkit: https://www.nongnu.org/oath-toolkit/download.html.
The steps are as follows, explained in more detail in sections below.
Use
oathtoolto register your terminal as a new sign-in app.Store and encrypt your Microsoft-generated secret key.
Use
oathtoolto generate a verification code each time you wish to log into the website that uses Microsoft MFA.Use the generated verification code in the website's login screen.
Register your terminal as a sign-in app
Click "Add sign-in method".
Click "Microsoft Authenticator".
Click "I want to use a different authenticator app" then "Next" then "Can't scan image?".
Copy the key next to "Secret key" then click "Next". Note you will need this secret key in a later step, so keep a copy of it.
Run:
oathtool --base32 --totp <INSERT SECRET KEY>Copy the 6 digit code into the box beneath "Enter the 6-digit code shown in the Authenticator app." on the Microsoft security info web page.
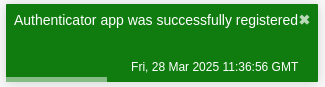
You should now see "Authenticator app was successfully registered" in the top right corner:
Encrypt your Microsoft-generated secret key
Now to automate verification code generation as a command in a shell script. First, store your secret key in an encrypted file.
Create a plain text file somewhere:
touch 2fa-passwdthen use a text editor to edit that to
2fa-passwdfile, pasting the secret key from earlier.Encrypt it:
gpg --output 2fa-passwd.gpg --symmetric 2fa-passwdGPG may ask you to input a password to encrypt this file. Whatever you type in will become the password you'll need to enter to decrypt your secret key (to generate MFA verification codes), so make a note of this GPG password.
Delete the plain text file:
rm 2fa-passwd
Generating verification codes with oathtool for future logins
Now create a shell command that decrypts your secret key and passes it to
oathtool to generate verification codes.
Create the shell script file:
touch 2fa-codeThen make it executable:
chmod 700 2fa-codeOptionally, create this file in a directory in your
$PATHso you can run2fa-codewithout having to specify its full path.Populate that file with this (modifying the path to your
2fa-passwd.gpgfile):#!/bin/sh gpg -q -d /path/to/2fa-passwd.gpg | oathtool --base32 --totp -
Using the verification code
When logging into the website that uses Microsoft MFA authentication:
Enter your username.
Enter your password.
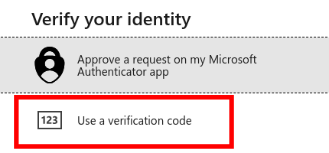
Click "I can't use my Microsoft Authenticator app right now"
Click "Use a verification code":
Generate the verification code by running your shell script file:
2fa-codeGPG may ask you for your GPG password to decrypt your
2fa-passwd.gpg. Type it in.A six-digit code will be printed to standard output. Type this into the website:
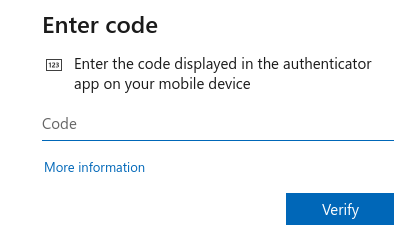
Then click "Verify".
You should now be logged into the website.
In future, you only need to follow this final step of "Using the verification code", i.e. run the
2fa-codefile to obtain a new six-digit code each time you are logging into the Microsoft-authenticated website.
Credit
These instructions are based on those shared by my colleague Swaraj Dash. I've just written them up for wider dissemination.